Nowadays, the digital world is more and more vulnerable to threats related to cybersecurity. Over the past years, the number of cyber attacks, including successful ones, have increased considerably. There are many different methods of becoming secure on the Internet. One of the basic, even fundamental, ways is a strong password. Have you ever wondered if your password is sufficiently secure? Are you sure that no unauthorised person has got to know it?
What passwords are secure?
A long password doesn’t always mean a secure password. For example, “hAix1111111111111111” theoretically contains 20 characters, but in practice it’s nearly as weak as “hAix1”, which has 5 characters. Many repetitions of the same character should be avoided.
“January2022!” is not a good solution either. Passwords related to a date are extremely popular, which is why you should avoid using the year and month name (the same applies to names of countries, towns, etc.).
You can come across lists of the most often used passwords on the Internet. If your password can be found on such a list, you must change it immediately.
Long random passwords such as “jD.3a>F!@91cHDGhh(*>236Phs##aA” are more secure. But how to memorise such a password? Will writing it down on a piece of paper or in a text file not be dangerous? As if it wasn’t enough, after a few months, when you can already remember it, the system will request you to change it…
What is a secure password that is easy to memorise?
The U.S. National Institute of Standards and Technology issued guidelines according to which a periodic password change is not recommended.
NIST argues that a password should be changed if you suspect that it has been compromised.
It’s also recommended to enable creation of passwords without a limitation of the number of characters.
A good practice is to use long sentences. “She.sells.sea.shells.but.more.money.more.problems” will be an effective password, which is easy to memorise. For instance, let’s compare it with the random password generated earlier: “jD.3a>F!@91cHDGhh(*>236Phs##aA”. If you want to check how much time can breaking a password take, go to www.passwordmonster.com.
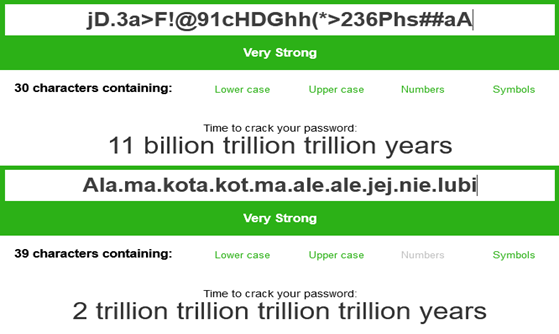
Conclusion? It takes considerably more time to break a long password that is easy to memorise than a shorter one that was generated randomly.
MFA – multi-factor authentication
Password is not the only line of defence. At present, many websites offer the possibility to configure the multi-factor authentication. Apart from a password, you can set up an additional authentication method.
These include in particular:
Security question – an additional question related to the account owner. Such questions refer to the place of birth or the favourite colour. This is the least secure method from among the listed ones. Often there are only a few such questions, so the chances that the hacker gets an answer right are high.
Authentication by telephone number – a code sent by a text message or a phone call received by the user on its telephone number. Such a solution is better than a security question but still vulnerable to phishing attacks.
Additional application – a code displayed in an application on a different device (e.g. smartphone, tablet) or a notification in an application, requiring the confirmation of the login attempt by the user. This solution protects from phishing better than the security question or authentication using the telephone number.
Biometrics – a scan of the fingerprints, face or voice recognition. This method requires having additional devices such as a fingerprint reader or a camera (they are built-in components of most of the contemporary computers or smartphones). This authentication method can be applied simultaneously with other methods. For example, in order to log in the Google account on an iPhone you have to enter your password and confirm the login in an authentication application only once. From that moment on, you won’t be asked to repeat this procedure each time you want to check your email. Instead, your telephone will be unlocked using your fingerprint or your face scan.
Dongles – additional authentication devices (most often connected to a USB port), which are the best protection from phishing at present. Physical contact of the user with the dongle is required to log in (you have to touch the device in the dedicated place).
If you have the opportunity to use MFA, don’t hesitate! This will considerably increase the security of your accounts. Even if someone learns your password, they won’t use it without the second authentication method.
Password manager
You should remember that it is a good practice to create a unique password for each account you use.
An average user can have a dozen or even several dozen accounts on various websites. So how to memorise several dozen different passwords? A password manager comes to the rescue – this software serves for secure password storage. Instead of memorising all passwords, it’s enough to memorise a single password for the manager. There are many such software products on the market today. Most software suppliers require you to purchase or subscribe for one but they offer also free plans (they are very limited, though).
As a rule, most password managers offer the following functions:
- Secure storage of encrypted passwords in the cloud
- Generation of secure passwords
- Check for password leaks
Depending on the software you use, you can expect also such functions as:
- Anti-phishing protection
- Facilitation of multi-factor authentication
- Possibility to store other sensitive data (credit card, personal data etc.)
It’s worthwhile to look at the following software: 1Password, Dashlane and LastPass. These products feature many functions that might prove extremely useful.
How should I know if my password has been compromised?
You’ll find many solutions on the Internet that will help you check if your password is still secure. These tools include the website haveibeenpwned.com. Thanks to it you can check if the password linked to the email address could have been compromised. It’s enough to enter the email address or the telephone number and generate a report. Apart from the information if our password has leaked, you receive also other data, such as: date of leak, full name, place of residence, telephone number.
To sum up, you have to act according to the following points so that your password is more secure:
- Use long passwords that are easy to memorise
- Avoid popular passwords and phrases
- Use multi-factor authentication
- Check regularly if the password has been compromised
- Use unique passwords for different accounts
- Use a password manager
As an IT company, Support Online has offered professional IT support for business for more than 20 years. With the customer security in mind, we have implemented ISO/IEC 27001 standards. Our many years’ experience has allowed us to develop methods and solutions to meet customers’ expectations in a best possible way. We take a customised approach, thanks to which the solutions we offer will enable your company’s growth.
Create an external IT department with us! We will take care of data security, user support and advise you on ways to make your company operate better.
Any questions? Call or write us.
Bartłomiej Róg
Administrator IT w Support Online



